Physical hacking tools used by many hackers
Physical hacking tools are superior to logical ones because they allow you to hack locally into a serverThe attackers can even allow us to enter a restricted area to which we do not have access, unlike the logical tools we normally use on our own machine, either connected to the network where we are going to carry out the attack or from another network.
Before we start I want to say that this post is not for the purpose of malicious acts, or for the purpose of doing harm against the integrity of a company or person, this post is for educational purposes and we simply want to show how hackers can use tools to achieve their goals, even ethical hackers use them for their own testing. Remember, no malicious purposes.
You have already seen 5 logical tools that every hacker should be able to master CLICKEA
Here are the Physical Hacking Tools
1. Lock Picking

The art of lock picking The tools to do this practice is practically to open padlocks or doors without the original key. Unlike computer hacking, this hacking you can feel how you break "the encryption" of each lock, for that reason hackers are very attracted to this practice. This practice is the worst when the person who use it, use it for malicious purposes, usually use it to commit a crime, but if you learn it for pleasure is a good practice and is even entertaining.
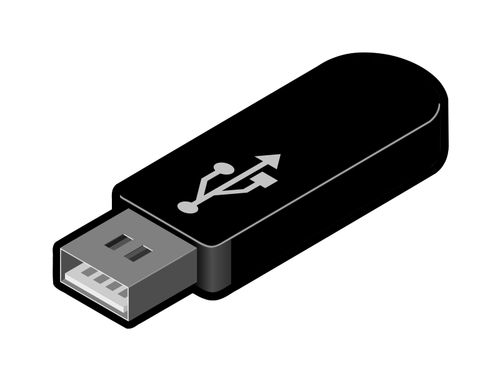
2. USB Rubber Ducky
A USB Rubber Ducky in simple view may look like an ordinary flash drive, a Rubber Ducky can be assembled at home, when you connect it to the computer is where the change to a conventional flash drive begins, A Rubber Ducky comes with a very small CPU when a computer is connected it starts writing to the computer in an automated way, to launch some software, malicious tools so that the victim's computer can be under its control. The PC can recognize it as a keyboard and can do powershell attacks.
3. Wi-Fi Pineapple

The PineApple wi-fi is to use it as a malicious Wi-Fi so to speak, hackers use it in shopping malls and monitor all users, allows DNS Spoofing attacks, review pages that we browse, perform Man In the Middle attacks and many types of attacks more.
4. Rasberry Pi

A Rasberry pi is a whole super small computer We can install any operating system on it, but it also has its own operating system Raspbian, which is a Linux distribution, its small size, can go unnoticed by the public and appears as another computer on any network without problems, so hackers now prefer to make instructions on the Rasberry Pi and connect them without anyone understanding that I use a computer. Also in the series Mr.Robot a series of computer security in a chapter appears a Rasberry Pi in the first chapters of the first season and prepare a zero day on it.
BONUS
Hardware keylogger

The current problem with Keyloggers is that the antivirus detects it easily, even recently I programmed a Keylogger in Python and my own operating system does not let me run it, but these Hardware keyloggers are very difficult to detect, because they are connected between the computer and the USB of the keyboard.
A keylogger can save all keystrokes, it can save our passwords and the most sophisticated keyloggers can even record the screen, take screenshots and send them via email.